In 2024, data privacy will be more important than ever. With increasing cyber threats and stricter regulations, selecting the correct web host is not only about uptime and speed but also about trusting a reliable guardian with your valuable data. This blog explores the essential aspects to think about, including strong security protocols, adherence to regulations, transparency, and user empowerment.
Importance of Data Privacy
1. Regulation & Enforcement
In 2023, there was a surge in enforcing existing data privacy regulations such as GDPR and CCPA, resulting in major companies facing substantial fines for not complying. This trend will continue in 2024, making data privacy a necessity for businesses.
New regulations are emerging worldwide, with variations at regional and national levels, making it essential for companies to navigate a complex landscape. Staying ahead of the game is crucial to avoid costly penalties and legal battles.
2. Growing Public Awareness
Data breaches and privacy scandals, like Facebook‘s Cambridge Analytica incident, have made individuals extremely conscious of the value and vulnerability of their data. Newsfeeds are filled with discussions about data misuse, fueling the public’s demand for stronger protections.
Furthermore, consumers are more inclined to boycott companies with weak data practices and actively seek out those that prioritize transparency and control. Ignoring public sentiment can harm a brand’s reputation and undermine customer trust.
3. Technological Advancements
Advancements such as AI and facial recognition offer immense potential but also raise new privacy concerns. These technologies can gather and analyze vast amounts of personal data, creating opportunities for misuse and discrimination.
We need robust data privacy frameworks to ensure the responsible development and use of these technologies, fostering innovation while safeguarding individual rights.
4. Cybersecurity Threats
The frequency and complexity of cyberattacks continue to increase, posing a threat to companies of all sizes. Data breaches have the potential to expose sensitive information, resulting in financial losses, damage to reputation, and legal consequences.
Implementing robust data security measures such as encryption, access controls, and incident response plans is essential to safeguard individual data and reduce potential risks. Investing in cybersecurity is no longer optional, but a critical requirement.
5. Competition for Trust
In today’s competitive landscape, consumer trust is more important than ever when it comes to data protection. Companies that prioritize data privacy gain a significant edge over their competitors.
Building trust and loyalty involves being transparent about data collection and usage, providing clear opt-out options, and ensuring easy access to personal information control. likewise neglecting data privacy can lead to customer alienation and impede business growth.
6. Impact on Individuals
Altogether Data privacy goes beyond mere compliance; it requires a human-centric approach that respects individuals’ rights to control their information and ensures their well-being. By making data privacy a priority, businesses exhibit ethical responsibility and dedication to safeguarding their users.
This commitment leads to stronger relationships, enhanced brand loyalty, and a more sustainable business model in the long term. Data privacy should be viewed not as a cost, but as an investment in trust and a healthier digital future.
Risks of Choosing the Wrong Web Host
Here are the reasons why selecting the incorrect web host can have negative consequences:
1. Security Vulnerabilities
Trustworthy hosts prioritize strong security measures to protect your data from unauthorized access. Opting for an unreliable provider can make you an easy target for hackers, malware, and data breaches. On the other hand, this could lead to the theft of financial data, compromised user accounts, and potential identity theft.
2. Unplanned Downtime and Data Loss
Picture your website suddenly going offline, impacting your online presence. Unstable hosts often experience frequent downtime, resulting in missed business opportunities and dissatisfied customers. Moreover, these downtimes may coincide with data loss, causing the permanent deletion of crucial information.
3. Compliance Challenges
With data privacy laws like GDPR and CCPA becoming more stringent, adhering to compliance standards is crucial. Non-compliant hosts put your data in jeopardy and expose you to significant penalties. Opting for a host unaware of these regulations can create compliance issues.
4. Inadequate Support
During technical difficulties, having a responsive and knowledgeable support team is essential. Unfortunately, some hosts provide subpar support, leaving you stranded with unresolved issues. This can waste valuable time and resources, impeding the growth of your website.
5. Limited Scalability
As your website expands, you require a host capable of seamless scalability. Above all choosing a host with limited capabilities can hinder your growth, necessitating a migration to a new provider in the future, and disrupting your online operations.
10 Deep-Dive Data Privacy Factors for Choosing a Web Host
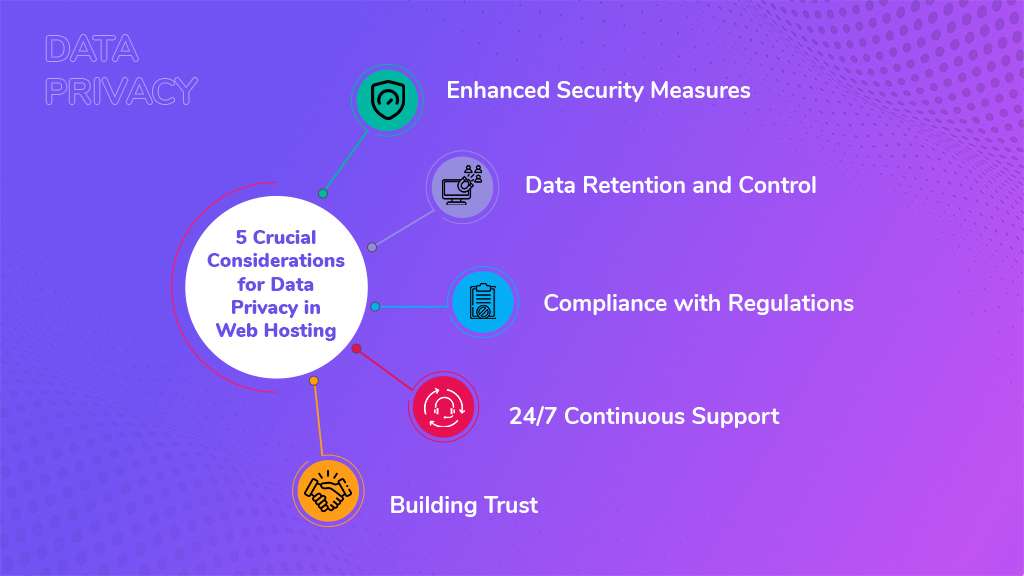
1. Enhancing Security Measures
i. Regular Audits and Penetration Testing
Don’t just settle for routine checks; delve into the frequency and approach. Seek out independent third-party audits to bolster your security measures.
ii. Multi-Factor Authentication (MFA)
Explore a variety of MFA solutions, such as hardware tokens or biometrics, and opt for a provider that offers customizable options to suit your requirements.
iii. SSL Certificates Verification
Scrutinize the certificate authority and validity duration. Consider advanced choices like Extended Validation (EV) certificates to enhance trustworthiness.
iv. Robust Firewall Protection
Comprehend the different types of protection available (e.g., web application firewall, intrusion detection/prevention systems) and their effectiveness against emerging threats.
v. Data Encryption Standards
Ensure encryption for stored and transferred data using strong algorithms like AES-256. Look into additional encryption methods like homomorphic encryption for safeguarding sensitive information.
2. Data Retention and Control
i. Data Retention Guidelines
Exercise caution with ambiguous statements; insist on precise timeframes for various data categories (e.g., logs, user data) and explicit criteria for deletion.
ii. Data Ownership Possibilities
Establish a transparent mechanism for asserting and transferring ownership of your data, if necessary. Familiarize yourself with potential constraints when utilizing open-source platforms.
iii. Data Erasure Alternatives
Ensure that the deletion procedure is irreversible, secure, and auditable. Inquire about self-service deletion alternatives and guarantees for data erasure.
3. Compliance with Regulations
i. GDPR and CCPA
When it comes to regulations such as GDPR, CCPA, and others, it is crucial to go beyond generic “compliance statements.” Instead, inquire about the specific steps taken to meet the requirements of each regulation. For instance, ask about measures implemented to uphold data subject access rights and breach notification protocols.
ii. Industry-Specific Regulations
Moreover, it is essential to delve into industry-specific regulations that may apply to your particular field. Conduct thorough research to identify any additional regulations relevant to your industry, such as healthcare or finance, and ensure that the hosting provider complies with them.
iii. Transparency about Certifications
In terms of transparency, it is advisable to seek out hosting providers that openly communicate their certifications. Look for internationally recognized certifications like ISO 27001 or SOC 2, so that they demonstrate a commitment to comprehensive security and privacy best practices.
4. Data Privacy Measures
i. Privacy Guidelines
Go beyond the complex legal language. Seek out straightforward descriptions of why data is collected, how it is shared, and what control users have.
ii. User Authority on Data
Verify precise control over accessing, correcting, and removing data. Explore options surely for opting out of marketing or sharing data with third parties.
iii. Clarity on Data Utilization
Don’t simply trust claims of data anonymization; grasp the potential uses or re-identification of anonymized data. Seek assurances of utilizing privacy-enhancing technologies such as differential privacy.
5. Backup and Recovery
i. Automated Backups
Verify the backup schedule, types of data being backed up, and where the data is stored. Hence consider implementing incremental backups to reduce potential data loss.
ii. Remote Backups
Maintain backups in a different geographical location from the main server for effective disaster recovery. Familiarize yourself with backup replication methods and security protocols.
iii. Efficient Recovery
Before any data loss event, test the recovery procedures. Evaluate the expected recovery durations and the ability to restore either specific data or entire datasets.
6. 24/7 Continuous Support
i. Continuous Availability
Confirm various contact options (phone, email, live chat) with quick response times, particularly outside of regular business hours.
ii. Specialized Knowledge
Make sure the support team includes experts in data security who are familiar with your unique requirements and industry standards.
iii. Transparent Communication
Seek regular notifications regarding security issues, maintenance plans, and possible weaknesses. Value proactive updates on new security risks.
7. Hosting Environment to Suit Your Needs
i. Shared Hosting
Take into account the potential risks associated with shared resources and opt for a provider that implements stringent isolation measures and security protocols. Additionally, consider managed shared hosting as it provides an extra layer of security.
ii. VPS Hosting
Carefully evaluate the level of isolation provided and the limitations on resource allocation when considering VPS hosting. It is crucial to ensure that the provider utilizes containerization technologies to enhance isolation.
iii. Dedicated Hosting
Although dedicated hosting offers more control, it is important to assess your technical expertise in managing security updates and patching diligently.
iv. Cloud Hosting
When selecting a cloud hosting provider, prioritize those with a strong security track record. Familiarize yourself with their data residency policies and encryption options for stored data.
8. Building Trust and Reputation
i. Customer Feedback
Take into consideration the feedback provided by users within your industry or those with similar data security requirements. Focus on comments that specifically address their experiences with data privacy.
ii. Recognition and Certifications in the Industry
Examine the credibility of the organizations that surely have awarded accolades and certifications to the service provider for their security and privacy measures. Also, delve into the specific criteria that the host has met to earn these accolades.
iii. Transparency Regarding Previous Security Incidents
Evaluate how the host has handled past security incidents, including their communication, efforts to resolve the issues, and the lessons they have learned from them. Henceforth, look for indications of their commitment to continuously improving their security practices.
9. Enhanced Capabilities
i. Security Auditing and Remediation
Implement regular and automated security audits along with immediate remediation processes. Explore the possibility of engaging penetration testing experts for comprehensive security evaluations.
ii. Data Protection Solutions
Examine features such as content monitoring, anomaly identification, and encryption for safeguarding data during transmission and storage. Assess the adaptability and personalization choices available for data protection policies.
iii. Emphasis on Secure Development
Question the provider’s dedication to secure development practices and staff education on security risks. Therefore, inquire about the availability of secure coding resources or frameworks to reduce the likelihood of coding mistakes.
10. Balancing Cost and Value
i. Emphasize Security and Adherence to Regulations
While evaluating features and costs, keep in mind that the most affordable option may not offer the highest level of security.
ii. Estimate the Potential Expenses of a Data Breach
Such expenses include penalties, harm to reputation, and loss of customers. These unforeseen costs particularly could surpass a slightly more expensive hosting solution.
iii. Seek out pricing structures that are clear and straightforward
Steer clear of undisclosed charges and grasp the financial impact of extra security measures or data storage needs.
Why BigCloudy is Your Data Privacy Partner?
In today’s world, where data breaches are a constant concern, BigCloudy explicitly offers a complete solution to protect your sensitive information. They offer the necessary tools and expertise to create a secure and reliable online environment, promoting customer trust and business prosperity.
1. Establishing Trust, One Secure Byte at a Time
In the current digital environment, gaining the trust of users is of utmost importance. BigCloudy goes above and beyond by not only providing SSL certificates but also empowering you to create a secure sanctuary for your customers’ data.
2. Unyielding Security for Your Card Information
BigCloudy indeed recognizes the significance of safeguarding sensitive financial data. Their mandatory SSL certificates encrypt all communication across entire websites, guaranteeing unwavering protection for credit card details, purchases, and online transactions.
3. No Room for Phishing
Phishing attacks are pervasive, targeting unsuspecting individuals everywhere. BigCloudy’s robust security measures significantly act as a shield, safeguarding your visitors from malicious scams. Rest assured, your website is indeed a safe and trusted space for everyone.
4. Multi-Domain Security
Managing multiple domains can be a security challenge. BigCloudy’s powerful Multi-Domain SSL certificates secure up to 100 hostnames under a single IP address. In general, this simplifies management and enhances security across your entire online presence.
5. PCI Compliance
BigCloudy takes PCI compliance seriously. Their SSL certificates adhere to the stringent security standards mandated by PCI-DSS, ensuring rock-solid protection for customer credentials and payments. In fact, they minimize the risk of breaches and boost customer confidence in your business.
Conclusion
In 2024, you don’t have to face the challenges of data privacy alone. BigCloudy is here especially to support you as a reliable partner, providing a strong defense for your important information. With top-notch security, strict compliance, and user-friendly controls, we enable you to establish a secure and worry-free environment. In conclusion, don’t compromise on safeguarding your data. Opt for BigCloudy, prioritize data privacy, and embrace a future where your online presence flourishes without any concerns.